As companies adopt work-from-home and BYOD policies, each remote device and user expands the attack surface. Zero trust cybersecurity systems offer tools that verify users, devices, and applications at the edge and encrypt data to prevent sensitive information from being compromised in a breach. This new security model includes substantial authentication requirements paired with multi-factor authentication (MFA) to protect credentials and continuous verification to detect changes in behavior. It also leverages network micro-segmentation to limit access between perimeters.
Page Contents
Compliance

Zero trust network access (ZTNA) focuses on “never trust, always verify.” Every user, device, and application must authenticate and continually revalidate their identity for every transaction. Once verified, access is granted to only those resources necessary for the task. This approach reduces attack surfaces by creating security perimeters around smaller areas of the network, preventing lateral movement. Zero Trust is a leading model and strategy adaptable for today’s remote work environment. By implementing ZTNA, organizations can mitigate risks and enhance their cybersecurity posture across multi-cloud environments. ZTNA solutions must support granular access controls and continuous threat monitoring to ensure compliance.
Additionally, they must be able to identify and mark devices that pose a risk. This allows companies to enforce policies and flag any unauthorized behavior. Additionally, ZTNA solutions must integrate with other security and networking technologies to deliver remote workers a unified, secure, and seamless experience.
Security
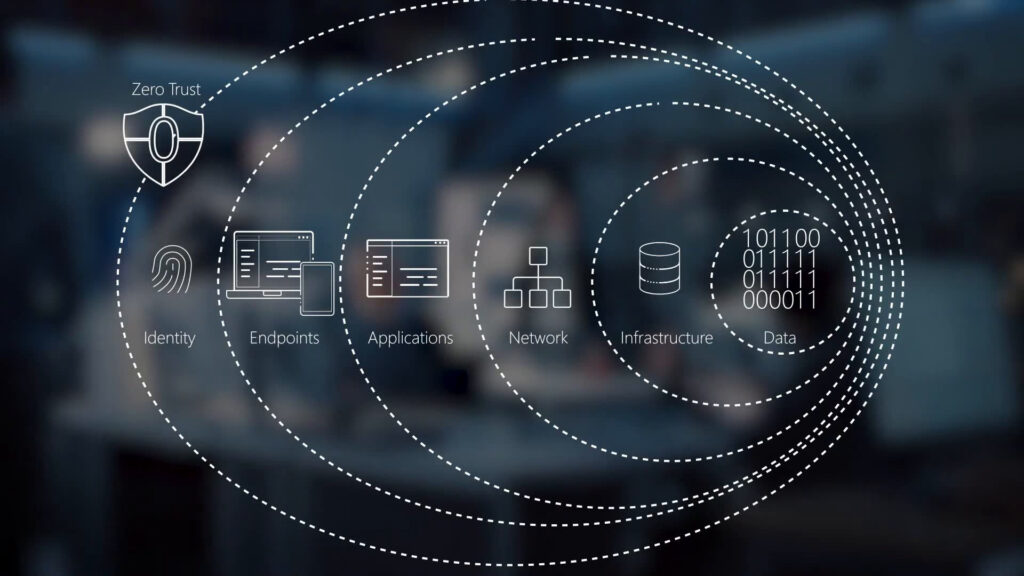
Zero Trust combines several advanced security technologies to protect remote workers and their devices. These include network micro-segmentation, strong authentication, and device and contextual flagging. Microsegmentation creates isolated perimeters for each business system, allowing connections within the perimeter but blocking access between them. This makes it harder for attackers to move laterally and target critical systems. Zero Trust also includes granular identity and access management, which allows enforcing policies based on user, device, and application. Another critical security feature of zero Trust is CASBs (compliance and assurance brokers). These solutions scan cloud-based software for compliance violations that might put agencies at risk. They can also prevent shadow IT by detecting unauthorized apps, flagging employees using them, and identifying potential risks. Finally, zero trust solutions offer a streamlined and frictionless login experience, whether employees are on the corporate network or not. This helps to remove any barriers that could inhibit productivity and reinforces a security mindset. In the age of remote work, every employee must understand their role in maintaining a secure environment. By providing training and awareness materials, you can help employees be proactive about preventing data breaches. You can encourage them to adopt best practices to reduce vulnerability and ensure they have the right tools and resources.
Flexibility

As more employees work remotely, the traditional security perimeter has become ineffective and impractical. Zero Trust replaces this model by creating multiple verification points, allowing only trusted devices and users to access critical data. This allows organizations to implement the security they need without hindering productivity. Zero trust solutions are designed to authenticate users and devices at every process step, from login to application use. This provides a strong layer of protection, even for remote workers who aren’t on the company network. Zero trust solutions also provide granular control over remote device health, ensuring that only devices that have passed a series of checks (such as those requiring anti-virus updates or those with an insufficient encryption posture) can gain access to the organization’s applications and infrastructure.
Moreover, the continuous authentication features in Zero Trust prevent attackers who have already penetrated a device or an application from moving laterally across the network. This drastically reduces the attack surface for any breach and helps to mitigate data loss. Zero trust solutions for remote work can be deployed in several ways, depending on the needs of each organization. For example, agent-based ZTNA requires software installation on the user’s device, while service-based models are provided as a cloud-native solution. In either case, it’s essential to communicate clearly with your remote workforce about the need for these security processes and how they work. This can help to ease employee concerns and encourage a positive security mindset.
Cost

The proliferation of work-from-home employees, digital nomads, and hybrid workers represents a significant challenge for security teams. Each new remote or mobile employee creates a potentially new entry point into the private network that traditional perimeter security models do not protect. Zero Trust removes the assumption that a user, device, or application is trusted by default and replaces it with an attitude of “never trust, always verify.” The process combines strong authentication, machine identification, and policy enforcement with the ability to monitor, filter, and log activity for signs of threat. This can be done in real-time, on both egress traffic going into the network and connections within it. In addition to requiring continuous authorization, zero-trust practices reduce the attack surface by using micro-segmentation to create smaller security perimeters around applications, workloads, and business-critical assets. They also employ least privilege access to restrict what users, devices, and apps can see and do on a network. This limits their access to tools and resources they do not need to perform a task and stops attackers who gain access from moving laterally across the organization. Implementing zero Trust can require a significant investment in technologies, processes, and tools to manage and maintain the security architecture. It also requires that organizations are prepared for the influx of work that may cause productivity to suffer initially as employees adjust to the new processes.






